
An Internal Intrusion Detection and Protection System by Using Data Mining and Forensic Techniques
Product Description
An Internal Intrusion Detection and Protection System by Using Data Mining and Forensic Techniques
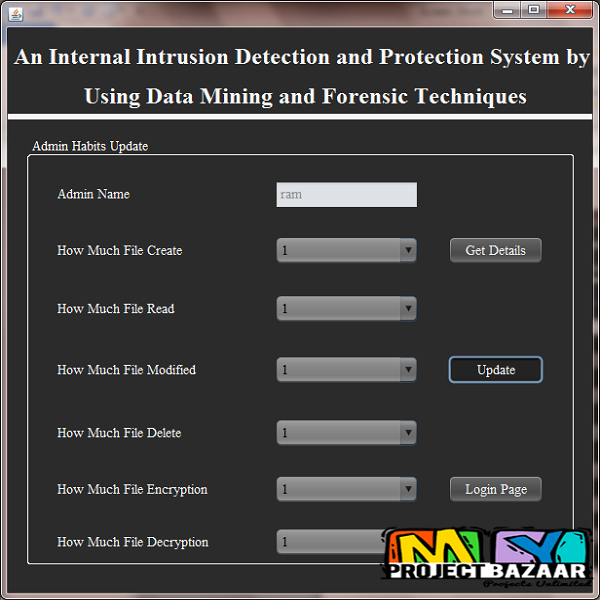
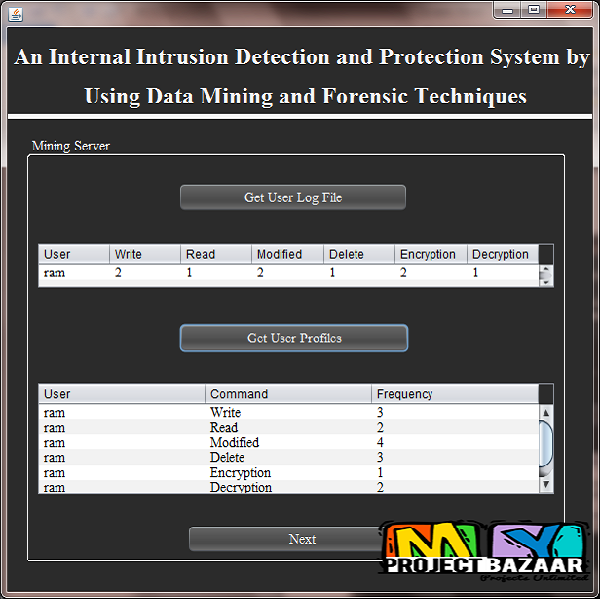
Abstract—Currently, most computer systems use user IDs and passwords as the login patterns to authenticate users. However, many people share their login patterns with coworkers and request these coworkers to assist co-tasks, thereby making the pattern as one of the weakest points of computer security. Insider attackers, the valid users of a system who attack the system internally, are hard to detect since most intrusion detection systems and firewalls dentify and isolate malicious behaviors launched from the outside world of the system only. In addition, some studies claimed that analyzing system calls (SCs) generated by commands can identify these commands, with which to accurately detect attacks, and attack patterns are the features of an attack. Therefore, in this paper, a security system, named the Internal Intrusion Detection and Protection System < Final Year Projects 2016 > IIDPS, is proposed to detect insider attacks at SC level by using data mining and forensic techniques. The IIDPS creates users’ personal profiles to keep track of users’ usage habits as their forensic features and determines whether a valid login user is the account holder or not by comparing his/her current computer usage behaviors with the patterns collected in the account holder’s personal profile.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |
Would you like to submit yours?















There are no reviews yet