Enabling Cloud Storage Auditing with Verifiable Outsourcing of Key Updates
Product Description
Enabling Cloud Storage Auditing with Verifiable
Outsourcing of Key Updates
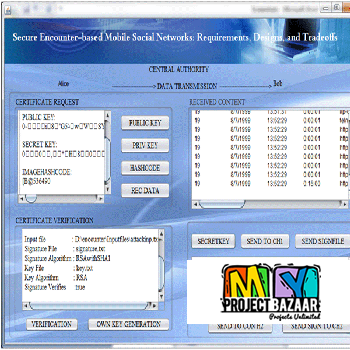
Abstract—Enabling Cloud Storage Auditing with Verifiable. Outsourcing of Key Updates Key-exposure resistance has always been an important issue for in-depth cyber defense in many security applications. Recently, how to deal with the key exposure problem in the settings of cloud storage auditing has been proposed and studied. To address the challenge, existing solutions all require the client to update his secret keys in every time period, which may inevitably bring in new local burdens to the client, especially those with limited computation resources such as mobile phones. we focus on how to make the key updates as transparent as possible for the client and propose a new paradigm called cloud storage auditing with verifiable outsourcing of key updates. In this paradigm, key updates can be safely outsourced to some authorized party, and thus the key-update burden on the client will be kept minimal. Specifically, we leverage the third party auditor < Final Year Projects 2016 > TPA in many existing public auditing designs, let it play the role of authorized party in our case, and make it in charge of both the storage auditing and the secure key updates for key-exposure resistance. In our design, TPA only needs to hold an encrypted version of the client’s secret key, while doing all these burdensome tasks on behalf of the client.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |