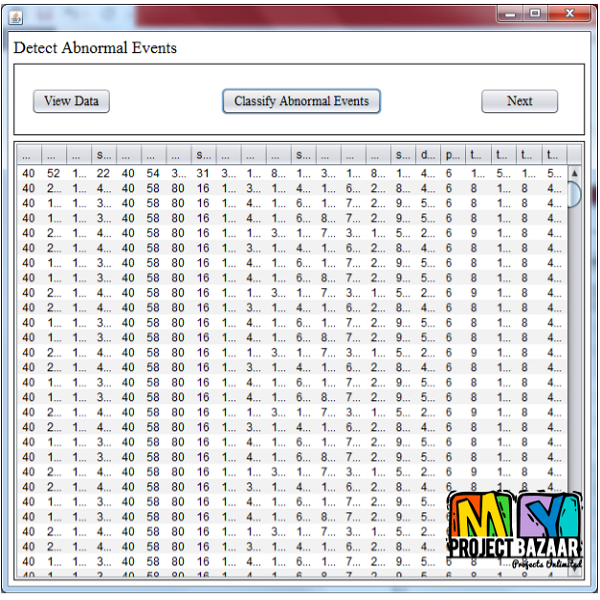
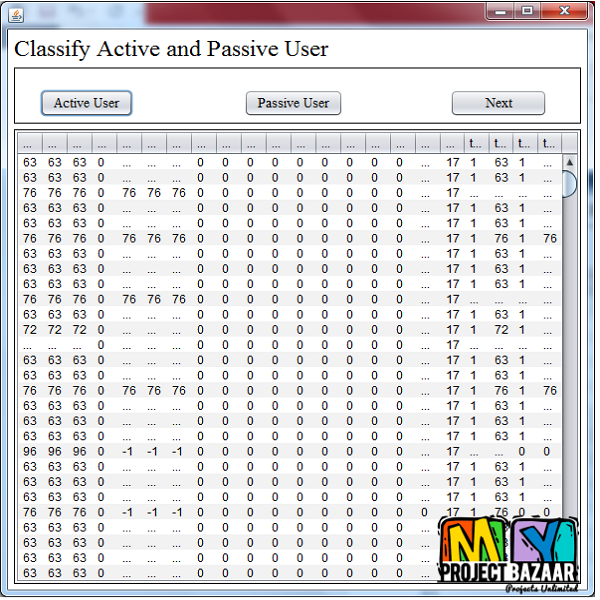
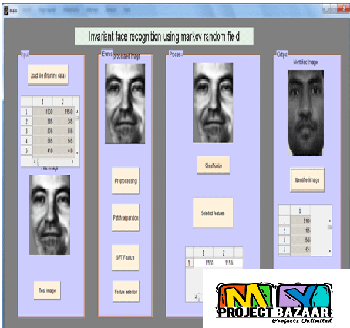
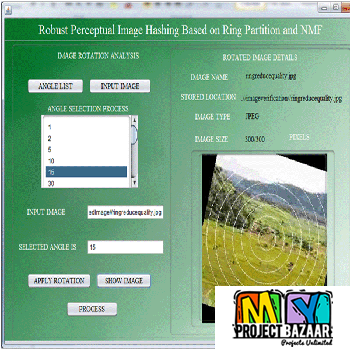
Deceptive Attack and Defense Game in Honeypot-enabled Networks for the Internet of Things
Product Description
Deceptive Attack and Defense Game in Honeypot-enabled Networks for the Internet of Things
Abstract— In modern days, breakthroughs in information and communications technologies lead to more and more devices of every imaginable type being connected to the Internet. This also strengthens the need for protection against cyber-attacks, as virtually any devices with a wireless connection could be vulnerable to malicious hacking attempts. Meanwhile, honeypot-based deception mechanism has been considered as one of the methods to ensure security for modern networks in the Internet of Things (IoT). In this paper, we address the problem of defending against attacks in honeypot-enabled networks by looking at a game-theoretic model of deception involving an attacker and a defender. The attacker may try to deceive the defender by employing different types of attacks ranging from a suspicious to a seemingly normal activity, while the defender in turn can make use of honeypots as a tool of deception to trap attackers. The problem is modeled as a Bayesian game of incomplete information, where equilibria are identified for both the one-shot game and the repeated game versions. Our results show that there is a threshold for the frequency of active attackers, above which both players will take deceptive actions and below which the defender can mix up his/her strategy while keeping the attacker’s success rate low. THE IOT, defined by the Oxford dictionary as “the interconnection via the Internet of computing devices embedded in everyday objects”, is envisioned to provide ubiquitous connectivity to an abundantly wide range of devices and systems. The IoT will serve as a conceptual background for future “smart” systems < final year projects >
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+