Composing Kerberos and Multimedia Internet KEYing (MIKEY) for AuthenticatedTransport of Group Keys
Product Description
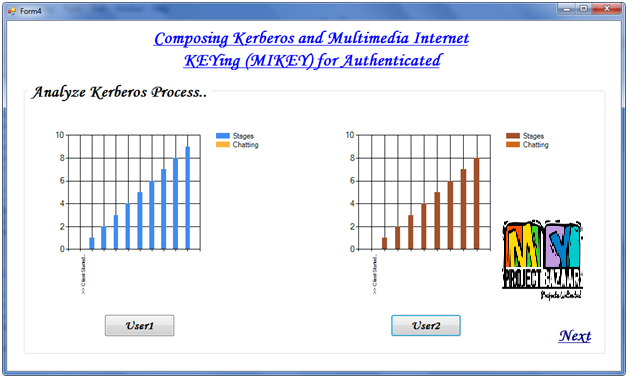
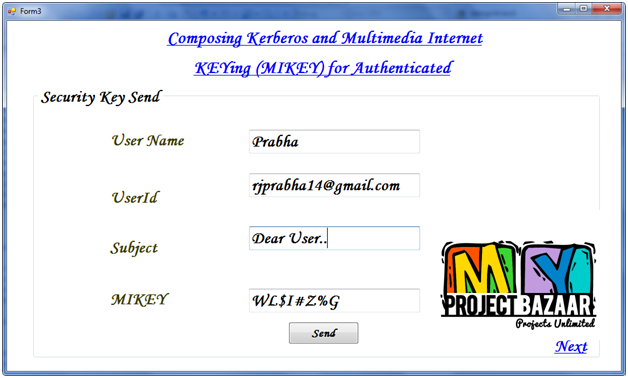
Abstract—Techniques to Minimize State Transfer Costs for Dynamic Execution Offloading in Mobile Cloud Computing. We motivate and present two designs for the composition of the authentication protocol, Kerberos, and the key transport protocol, Multimedia Internet KEYing (MIKEY) for authenticated transport of cryptographic keys for secure group-communication in enterprise and public-safety settings. A technical challenge, and our main contribution, is the analysis of the security of the composition. Towards this, we design our compositions to have intuitive appeal and thereby less prone to security vulnerabilities. We then employ protocol composition logic (PCL), a state-of-the-art approach for analyzing our composition. For this, we first articulate two properties that are of interest. Both properties are on the group key that is transported; we call them Group Key Confidentiality and Acquisition. Group Key Confidentiality is the property that if a principal possesses the key, then it is an authorized member of the group. Group Key Acquisition is the property that if a principal is a member of the group, then it is able to acquire the group key. In the course of our rigorous analysis, < Final Year Projects > we discovered a flaw in our first design, which we point out, and which lead us to our second design. We have implemented both designs starting with the publicly available reference implementation of Kerberos, and an open-source implementation of MIKEY. Our implementations are available as open-source. We discuss our experience from the implementation, and present empirical results.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |