
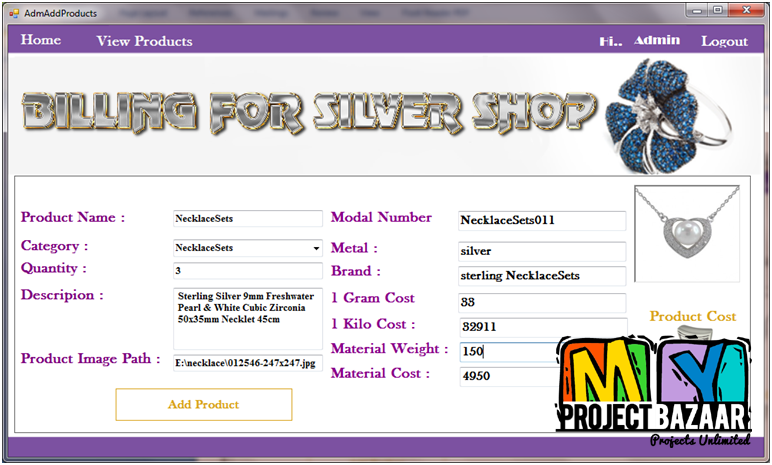
Billing For Silvershop
Product Description
Abstract—Billing For Silvershop. Mobile devices are evolving and becoming increasingly popular over the last few years. This growth, however, has exposed mobile devices to a large number of security threats. Malware installed in smartphones can be used for a variety of malicious purposes, including stealing personal data, sending spam SMSs, and launching Denial of Service (DoS) attacks against core network components. Authentication and access-control-based techniques, employed by network operators fail to provide integral protection against malware threats. In order to solve this issue, the activity of each mobile device in the network must be taken into account, < Final Year Projects > and combined with the activities of all the other devices. The communication activity in the mobile network has a source, a destination, and possibly communication weights (e.g., the number of calls between two mobile devices). This relational nature of the communication activity is naturally represented with graphs. This indicates that graphs can be utilized in order to provide better representations of the entire network activity, and lead to better detection results when compared to methods that consider the activity of each mobile device individually.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |
Would you like to submit yours?















There are no reviews yet