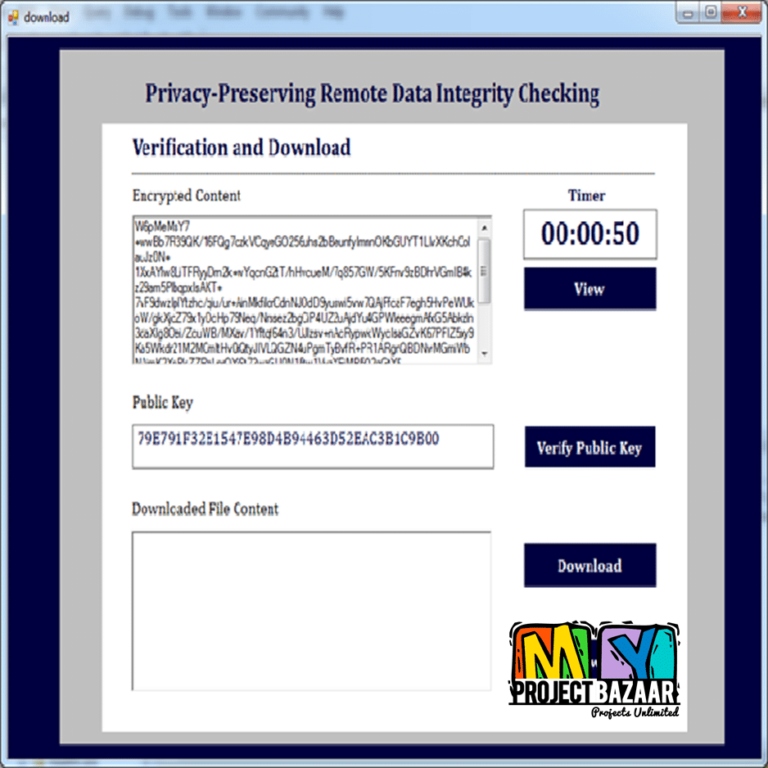
Security Protocols Involved in Mobile Computing Projects to Overcome Malicious Attack
Mobile Computing Protocols The Malicious attack is an endeavor to emphatically abuse or take advantage of some computer system. Whether through computer viruses, social engineering, phishing or other types of social engineering. Since they are done with the intent of stealing personal information or to reducing the functionality of targeting Mobile Computing Projects. Mobile Computing…