Vulnerable Concealed Map-Reading Inside Mobile Ad Hoc Networks
Product Description
Vulnerable Concealed Map-Reading Inside Mobile Ad Hoc Networks
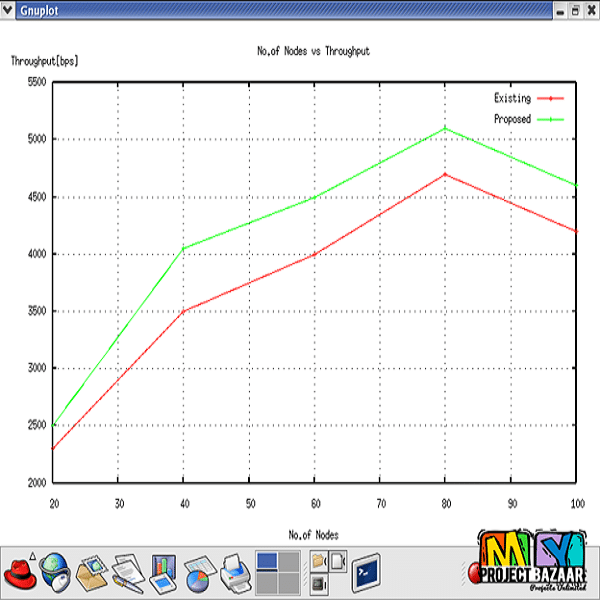
Abstract-Number of techniques has been used based on packet encryption to protect the data forwarding in MANETs, Still MANETs are attacked by hackers. To get over these attack a new technique called statistical traffic pattern discovery system can be used. It is an approach to discover entire raw traffic by using probability of traffic characteristics. It discover the relationships of source to destination communication. Maximum in wireless ad hoc network, it will always choose shortest path in prior. So attackers shall enter the network freely, because if the node monitors the packet forwarding mechanism it can easily identify the entire traffic pattern in the system. Based on the activity of hacker will enter the network effectively. It can be helpful for dropping or modifying data. But here we choose the second shortest path for data forwarding. In our scenario when we change to select the routing path hackers can’t be capture the current routing path.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |