Ver ifiable and Exculpable Outsourced Attribute-Based Encryption for Access Control in Cloud Computing
Product Description
Verifiable and Exculpable Outsourced
Attribute-Based Encr yption for Access Control
in Cloud Computing
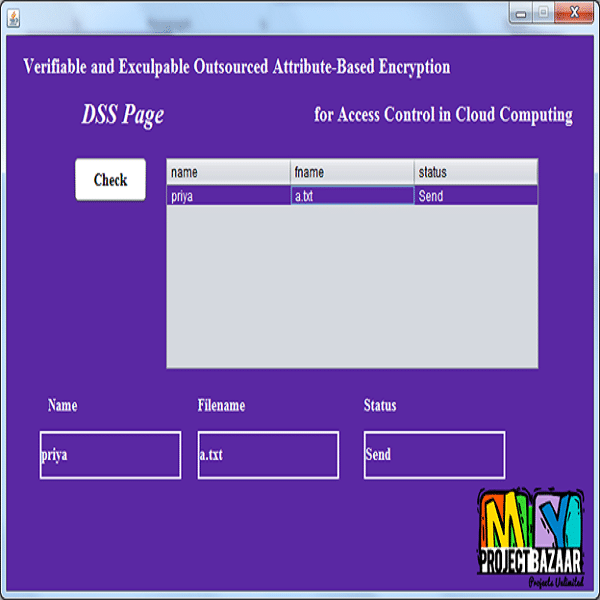
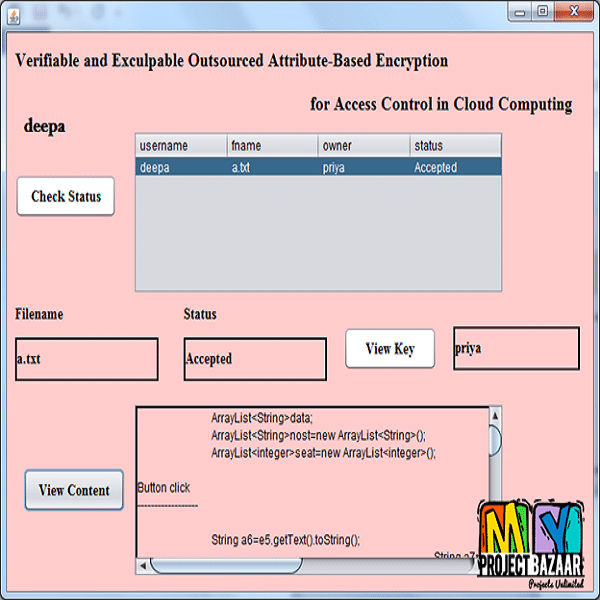
Abstract-In the first place, propose two ciphertext-policy attribute-based key encapsulation mechanism (CP-AB-KEM) schemes that for the first time achieve both outsourced encryption and outsourced decryption in two system storage models and give corresponding security analysis. In our schemes, heavy computations are outsourced to Encryption Service Providers (ESPs) or Decryption Service Providers (DSPs), leaving only one modular exponentiation computation for the sender or the receiver. Moreover, we propose a general verification mechanism for a wide class of ciphertext-policy (cf. key-policy) AB-KEM schemes, which can check the correctness of the outsourced encryption and decryption efficiently. Concretely, we introduce a stronger version of verifiability (cf. [1]) and a new security notion for outsourced decryption called exculpability, which guarantees that a user cannot accuse DSP of returning incorrect results while it is not the case. With all these mechanisms, any dispute between a user and an outsource computation service provider can be easily resolved, furthermore, a service provider will be less motivated to give out wrong results. Finally, we implement our schemes, and the results indicate that the proposed schemes/mechanisms are efficient and practical.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |