
Ensuring Data Privacy and Access Anonymity using Cryptographic Techniques in Cloud Computing
Product Description
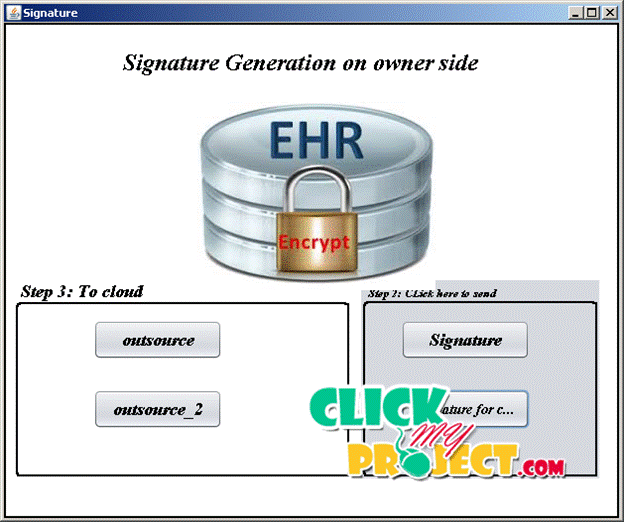
Abstract—Ensuring Data Privacy and Access Anonymity using Cryptographic Techniques in Cloud Computing. Cloud computing is the one which offers infrastructure to the client on a pay as you use model by leveraging on the Internet technology. As this model depicts the electricity billing it is often termed as utility computing. It offers various services to the client < Final Year Projects > based on the need. The need of the resources can be scaled up or down on the basis of the requirement. The IT sectors started using cloud service models. As the use of cloud increases day by day the concerns of cloud also gets increased. There are number of data breaches that are happening day by day that affect the cloud growth. The major concern in adapting cloud is its security. The companies have lot of data that gets increased each day enlarges the complication of data privacy and security. The data that we talk can be classified as either stagnant data i.e., for simple storage as offered by Amazon’s Simple Storage Service (S3) or it can be vibrant that changes often. The solution available to protect the stagnant data will be to simply encrypt the data before it gets stored in the server. In order to solve the issues of vibrant data the techniques are being proposed to work out on the encrypted. This paper is a survey of different security issues that affects the cloud environment and related work that are carried out in the area of integrity. The technique proposed combines the encrypting mechanism along with the data integrity check mechanism. The data are double wrapped to ensure no data leakage happens at the server side. The data are also shared with users with proper access mechanism.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+Additional Information
| Domains | |
|---|---|
| Programming Language |
Would you like to submit yours?
















There are no reviews yet