Revocable Identity Based Access Control for Big Data with Verifiable Outsourced Computing
Product Description
Revocable Identity-Based Access Control for Big Data with Verifiable Outsourced Computing
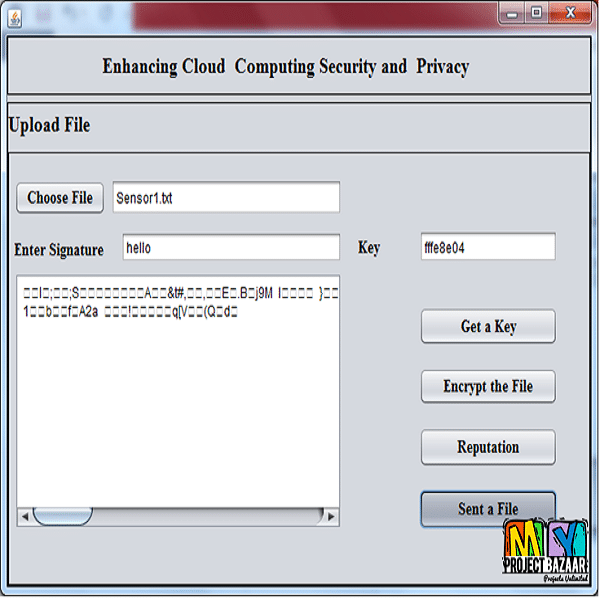
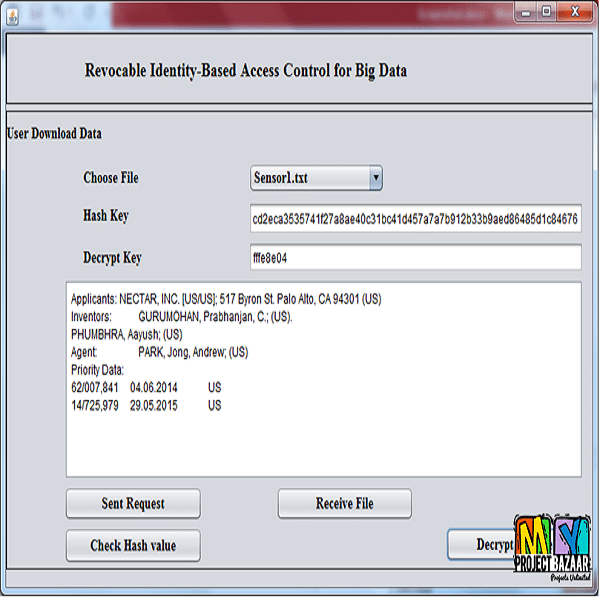
Abstract– To be able to leverage big data to achieve enhanced strategic insight, process optimization and make informed decision, we need to be an efficient access control mechanism for ensuring end-to-end security of such information asset. Signcryption is one of several promising techniques to simultaneously achieve big data confidentiality and authenticity. However, sign- cryption suffers from the limitation of not being able to revoke users from a large-scale system efficiently. First identity-based (ID-based) signcryption scheme with efficient revocation as well as the feature to outsource unsigncryption to enable secure big data communications be- tween data collectors and data analytical system(s). Our scheme is designed to achieve end-to-end confidentiality, authentication, non-repudiation, and integrity simultaneously, while providing scalable revocation functionality such that the overhead demand- ed by the private key generator (PKG) in the key-update phase only increases logarithmically based on the cardiality of users. Although in our scheme the majority of the unsigncryption tasks are outsourced to an untrusted cloud server, this approach does not affect the security of the proposed scheme. We then prove the security of our scheme, as well as demonstrating its utility using simulations.
Including Packages
Our Specialization
Support Service
Statistical Report

satisfied customers
3,589
Freelance projects
983
sales on Site
11,021
developers
175+